V1 Instruction
Server Setup Manual
|
Content |
Parameter |
|
Model No |
iPollo V1 |
|
Crypto Algorithm /coin |
Ethash/ETH |
|
Hashrate(MH/s) |
3600 (±10%) |
|
Operation temperature(℃) |
10-25 |
|
Power consumption(W) |
3100(±10%) |
|
Memory |
Design memory-6 GB, available memory-5.8 GB |
- V1 : Check Before Use
- Sign ForInspection
- When signing for the new server, please check whether the appearance of the package is damaged. If there is any damage, please take a picture and contact our after-sales service.
- After openingthe package, please check whether the server case is deformed, whether the fan and connecting cable are damaged, and whether the cable is damaged. If there is any damage, please take a picture and contact our after-sales service.
- Please check whether there is any abnormal sound on the server. If there is any abnormal sound, please contact our after-sales service.

- After-sales contact information
- Official Website: ipollo.com
- Official Wechat Account:iPollo
- Facebook:@iPolloMiner
- Twitter:@iPolloMiner
- E-mail:support@ipollo.com
- Notes
- Recommended ambient temperature range: 10℃-25℃.
- The hashrate is subject to the 24-hour hashrate of the Mining Pool.
- Pay attention to dust and suchobjects, so as not to corrode the computing board or affect the heat dissipation of the server.
- It is recommended to use Google browser or Firefox browser to browse the server background.
- It is strictly forbidden to plug and unplug the power cable and signal cable under power. The AC side of the power supply ofthe server must be reliably grounded.
- V1 : Product Introduction
- Main Components

- “1”: power adapter(the pictures are for reference only, please refer to actual products.)
- “2”: fan
- “3”: V1
- Interface Introduction

|
Fault |
The fault warning light. In most cases, when this light flashes, it indicates that a fault has occurred |
|
Normal |
Running indicator light. In most cases, when this light is on, it indicates that the machine is working normally |
|
Reset |
Server factory reset button |
|
IP Report |
Use the show IP software to feed back the IP of this server to the computer |
|
TF card |
SD card slot |
|
ETH |
Network interface |
- Notes
- In the process of running the server, please place it as shown in the picture below, that is, keep it flat to avoid any damage to the server.

- The socket shall be installed near the server and shall be easily accessible.
- The power input of this product is 200~240VAC 50/60Hz 16A. When the product is powered off, you need to turn off the power switch first.
- For your safety, it is forbidden to remove any screws on the server.
- Do not press the metal buttons on the casing.
- V1 : Use and Configuration
- Server Connection
- Power Connection
The power input of V1 is 200~240VAC 50/60Hz 16A, the server can work normally after connecting correctly with the cable.


- InternetConnection
(2-1) Wired Connection
The interface marked “ETH” on the server panel is the network cable interface. Pay attention to the direction when inserting the cable. Please insert the crystal head in place. After inserting it in place, you will usually hear a light “click” sound.

- Log in to the Server
2.1 Find the server IP
After the server is powered on and connected to the Internet, it begins to start. After the server’s normal light is on, you can find the IP of the server. You can use the “show IP” software to find the server IP as follows:
- Download software: ShowIP
- Double-click “show IP” to open the software.
- Short press the “IP Report” button on the server for 1 second and release it.
- The server IP information is fed back on the PC, as shown below:

Note: The server and PC must be in the same network segment, otherwise the IP information returned by the server cannot be received.
2.2 Enter the Server Background Management System
- After finding the IP of the server, enter the obtained IP address in the browser (Google is recommended), press Enter to enter the server login interface, and enter the default administrator account and password: root

- press “Login” to enter the Server Backstage Management Systemas follows:
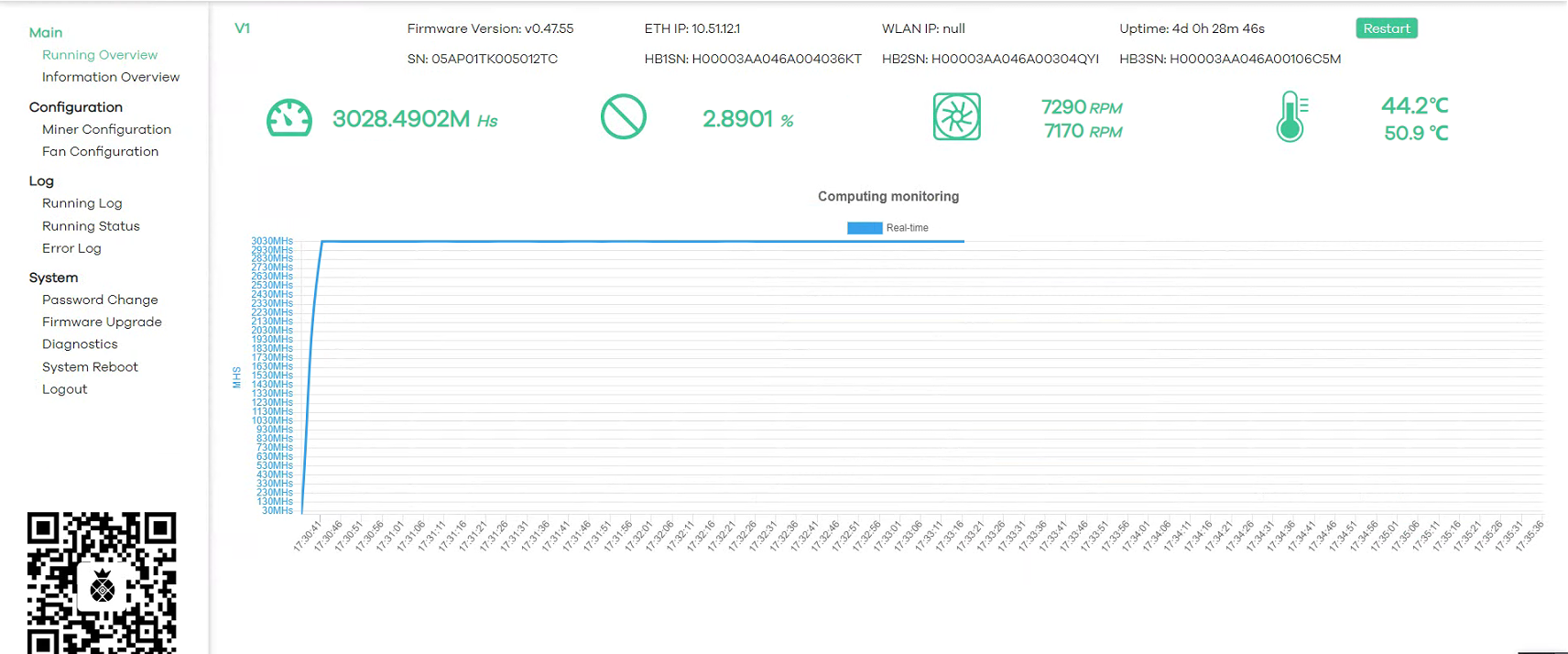
- Server Settings
Click the "Miner Configuration" interface under "Configuration" to set the "Mining Pool" and "Network"

3.1 Fill in the Mining Pool Information
Note: This manual takes the “poolin” as an example.
ETH mining address: stratum+tcp://eth.ss.poolin.one:443
(1)Select "Pool Configuration" and fill in the Mining Pool Information
(1-1) The "Url" in "Mining Pool 1" is filled with the ETH poolin mining link address: stratum+tcp://eth.ss.poolin.one:443
(1-2) "Worker" in "Pool 1" fills in "ipollomini.001"; "ipollomini" is a custom "sub-account" in the corresponding Mining Pool account; the number suffixed with ".001" is the number used to distinguish the server;).
Note: For customization such as numbers or letter combinations, use English periods to separate them, only modify the corresponding characters, and do not increase or decrease spaces and punctuation)
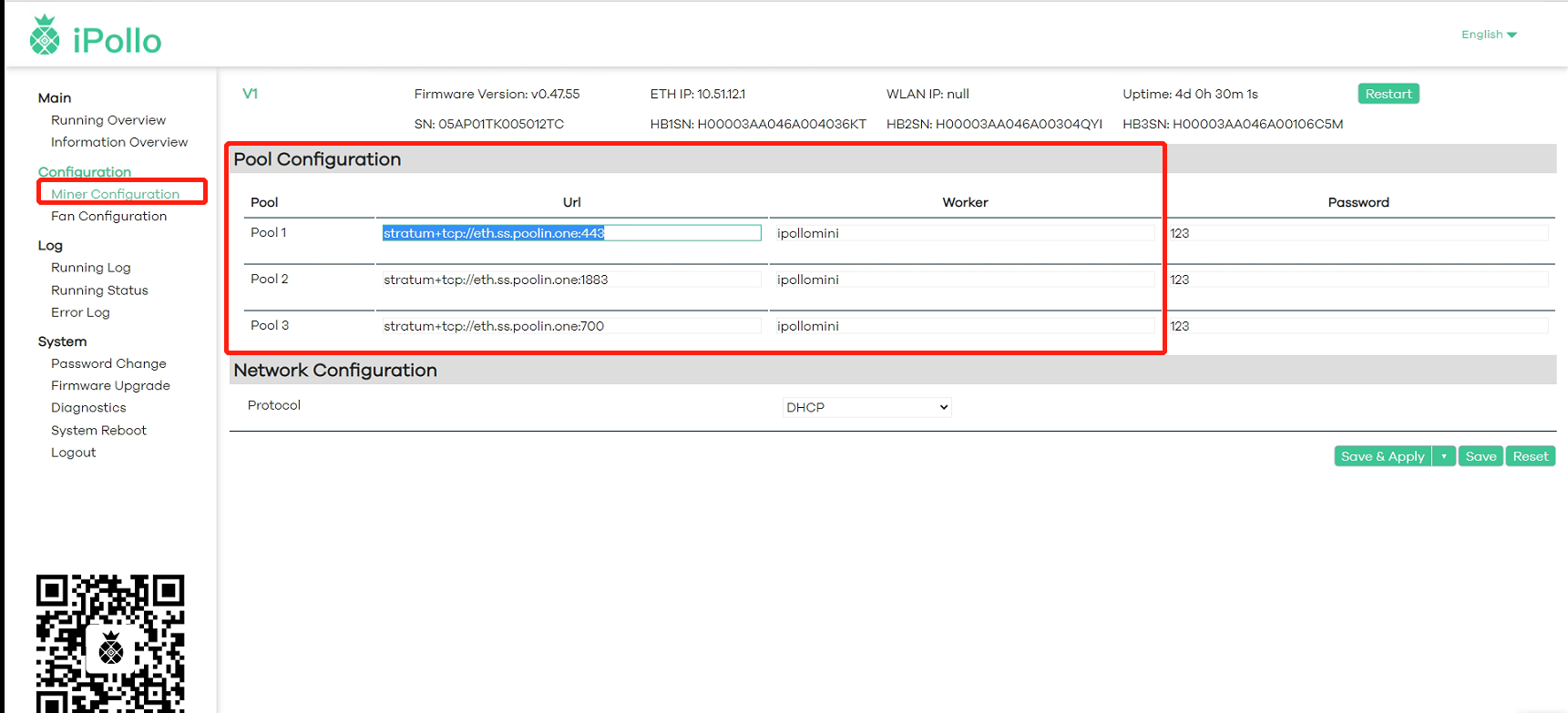
Note: In order to prevent “Pool 1” from being disconnected, it is recommended to set “Pool 2” and “Pool 3” at the same time, so as to ensure that the system will automatically switch to “Pool 2” or "Pool 3” for normal operation when “Pool 1” goes offline.
3.2 Network Settings
(1) Select “Network Configuration” and fill in the network information:
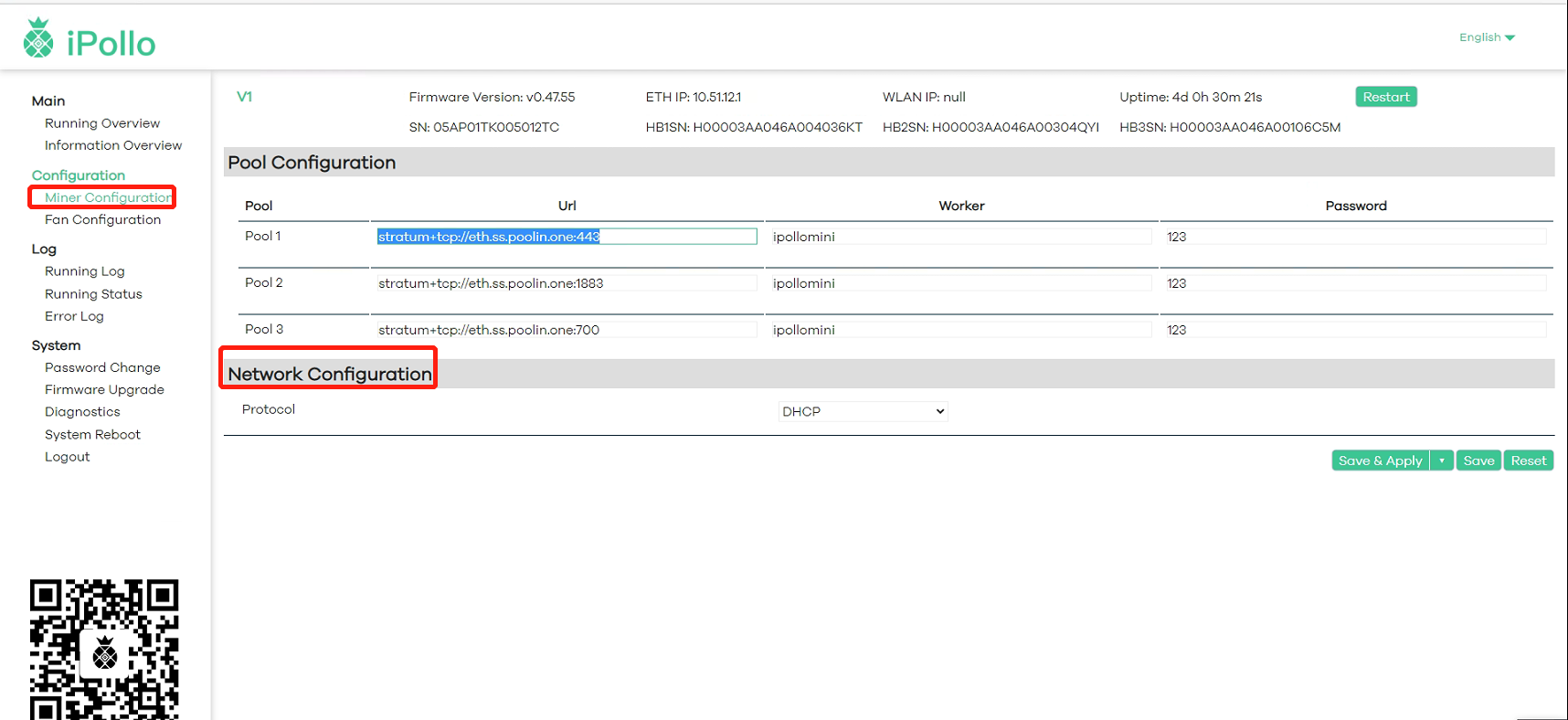
(2) In the protocol column, select one of “DHCP (dynamic)” or “Static” (optional).
(2-1) Select “DHCP (Dynamic)” State:The server automatically obtains an IP address
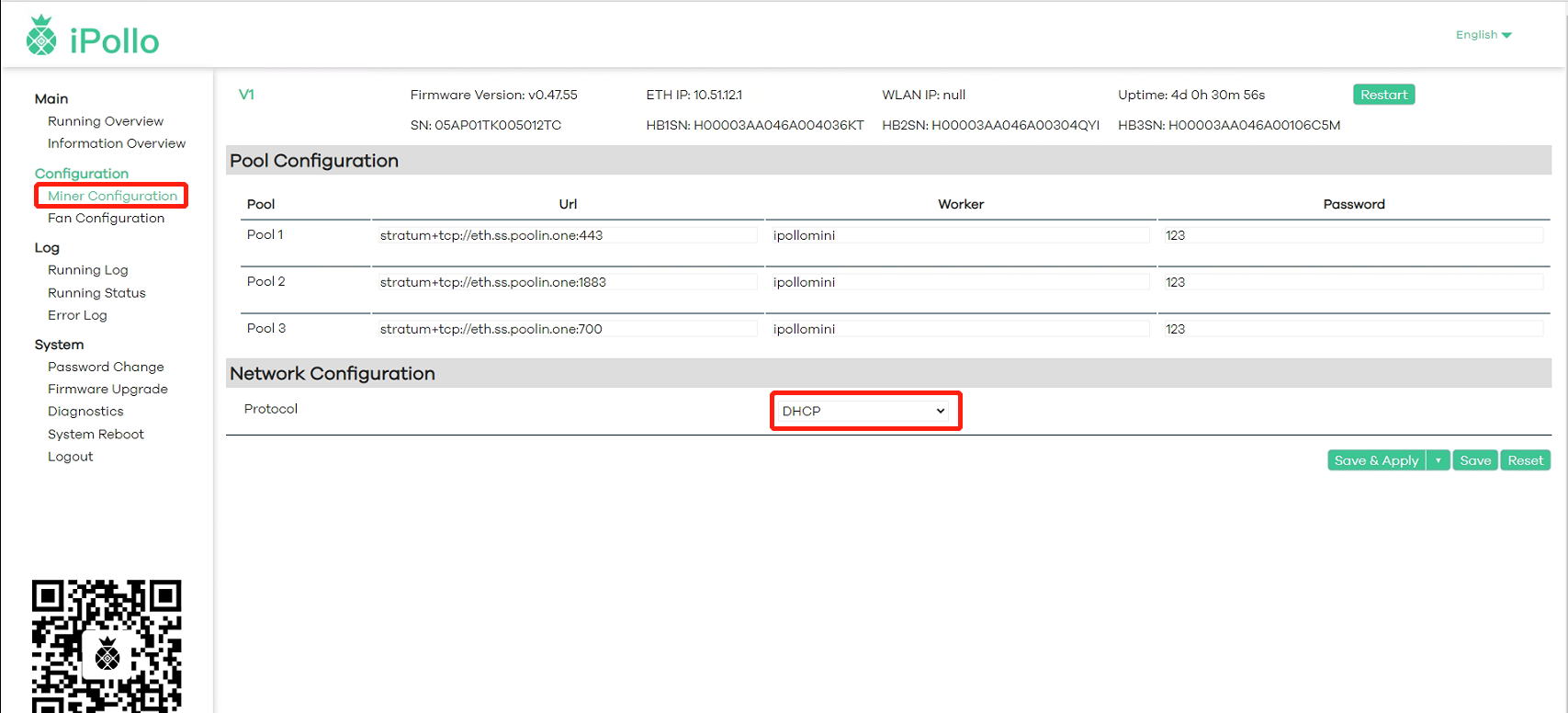
After setting, click “SAVE&APPLY”, the system will save and automatically restart to take effect, and the server will start to run normally.
End here, the configuration of the server has been completed, congratulations on your becoming a miner.
(2-2) Select “Static” State
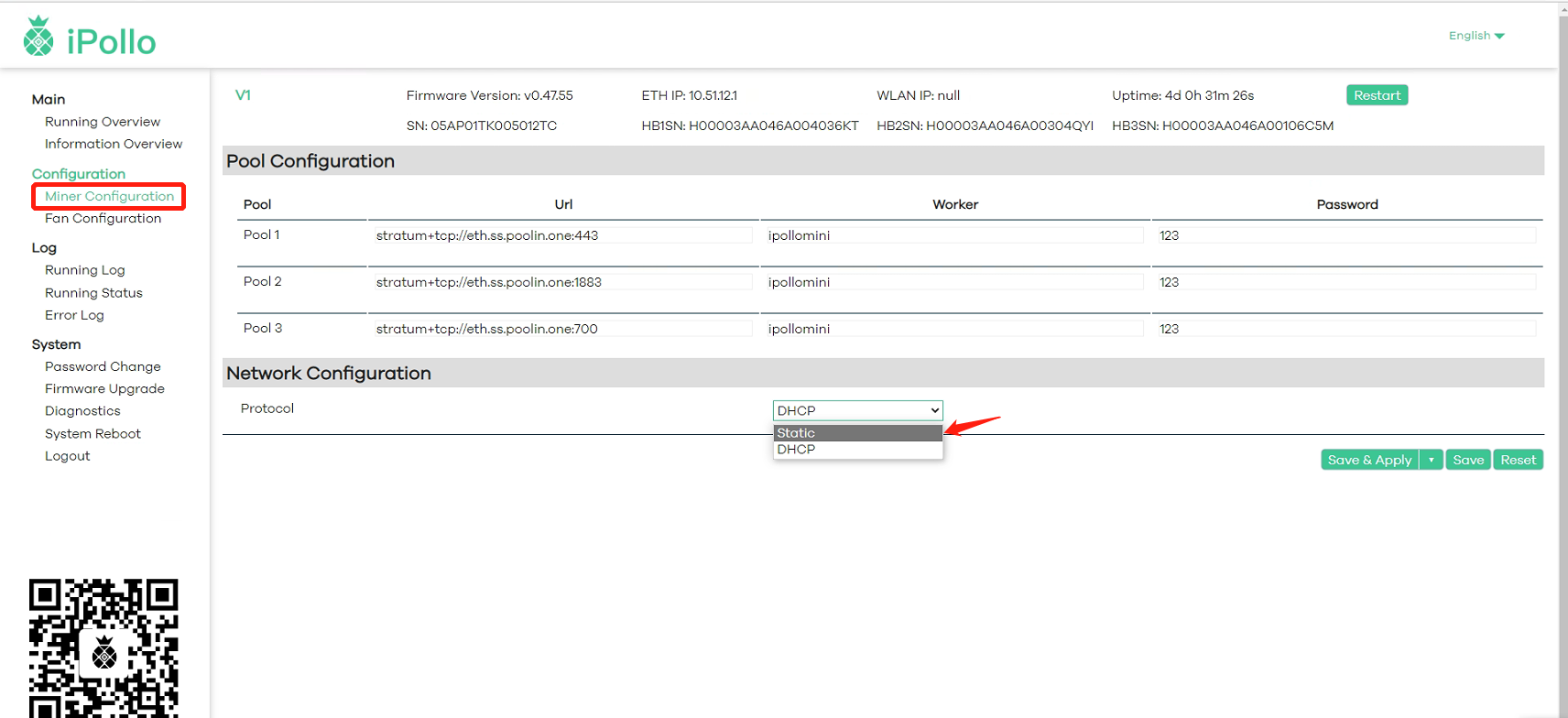
- Enter the IP address, netmask, gateway, and DNS-Server in turn in the four boxes below, then click “SAVE&APPLY”.
- After the page buffering is completed,the configuration of the server has been completed, congratulations on your becoming a miner.

Image (Static)
Note: The protocol information filled in "Network Configuration" in the figure (static) is for reference only, please refer to the on-site network protocol information for details.
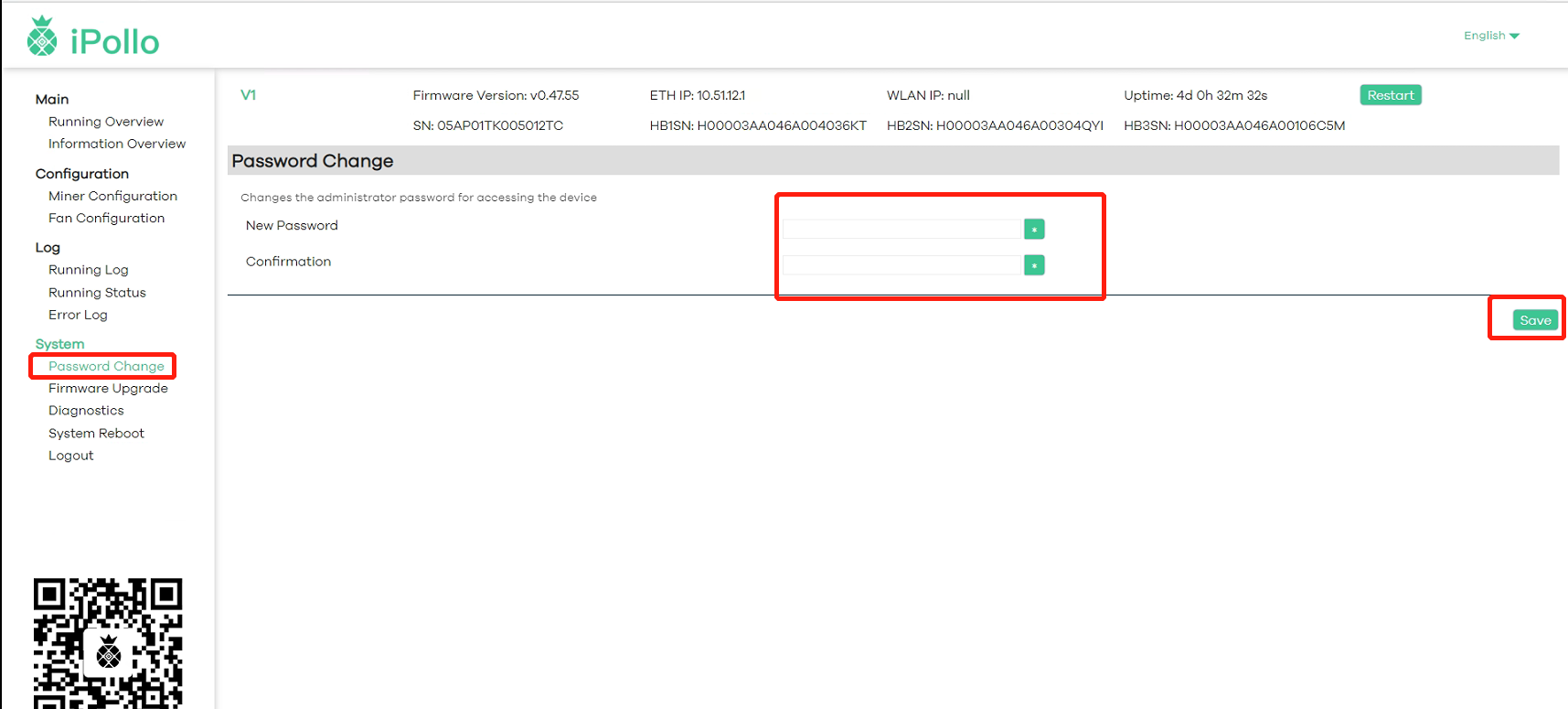
3.3 Login Password Modification
If you need to change the server login password, the operation method is as follows:
- The server is powered on and connected to the network;
- Through the browser (Google), enter the server IP account password and login information in turn to enter the server web page background;
- Click "System" and select " Password Change ";
- Enter the modified new password in “New Password”, and enter the modified new password again in “Confirmation”, and then click “SAVE” below to take effect:
Note: The “poolin” mining pool is used as an example above. If you use other mining pools, please modify it to the address of the mining pool you want to use and refer to the corresponding mining pool operation instructions.
- WARNING
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device will not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation.
Caution: Changes or modifications not authorized by the responsible party could void the user's authority to operate the equipment.
NOTE:This equipment has been tested and it complies with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment will generate, use and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to wireless radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception when turning the equipment off and on, the user is encouraged to try to deal with the interference by one or more of the following measures:
--Reorient or relocate the receiving antenna.
--Increase the space between the equipment and receiver.
--Connect the equipment into an outlet on a circuit different from that the one the receiver is connected.
--Consult the dealer or an experienced radio/TV technician for help.
- Notice
- After the machine is running normally, please use the "24-hour hashrate of the Mining Pool" as the criterion.
- It is recommended to use the original standard power supply to avoid damage to the machine or any safetyaccidents.
- Try to use the original standard power supply to suppress the voltage shock at the moment of power-on.
- Please be careful not to spill water or other liquids on the machine, especially the inner parts.
- Please pay attention to ventilation and heat dissipation, do not block the ventsor place the device on flammable materials and fabrics.
- If you need to disassemble the case to check the problem, pleasecontact iPollo customer service at first. If you open the case without permission, the warranty will be voided.
- This device is not for family consumption. This device shall be operated only by professionals.Nonprofessionals (such as adolescents, ETH.) are not allowed to operate this device. In case of breaching this notice, the breaching person shall be responsible for any loss or damage caused to others or himself/herself.
- Youshall be liable for any loss or damage caused to yourself arising from or caused by algorithm change of block-chain itself or the device’ algorithm change made by yourself. In such case, the device will not enjoy the official warranty service and will be treated as out-of-warranty.
- Due to the nature of the Ethash/Etchash algorithm mechanism, the size of the DAG file gradually increases over time in the network. Once the size of the DAG file exceeds the memory capacity of the machine, it will no longer be able to mine the specified coin. Please note that this scenario will not be taken into consideration within the scope of our company's return and warranty services. There might be a risk in a potential loss of income, depending on the volatility of the crypto market. This risk has been addressed and shall be borne by the customer.
- All final interpretation rights of this product are reserved by IpolloHK Limited.
